In today’s rapidly evolving cloud environments, organizations often operate multiple AWS accounts — each representing separate projects, departments, or workloads. With this increased account segregation, securely managing access across accounts becomes vital. That’s where AWS IAM Cross-Account Access comes into play.
This article explores AWS IAM cross account access best practices (Identity and Access Management) in depth, its use cases that you should follow in 2025 to keep your AWS environment secure, scalable, and compliant.
Table of Contents
What is Cross-Account Access in AWS IAM?
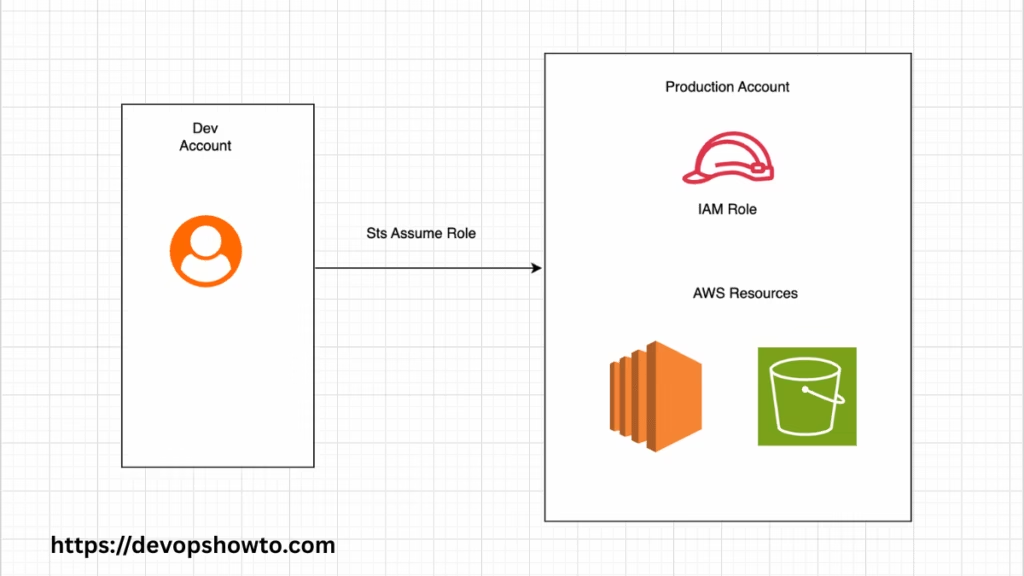
Cross-account access enables resources or users in one AWS account (Account A) to access resources in another AWS account (Account B) securely, without needing to create duplicate IAM users.
Instead of managing separate user credentials in each account, you can grant access using IAM roles and trust policies, allowing users to assume roles in another account.
Real-World Use Cases of IAM Cross-Account Access
IAM (Identity and Access Management) Cross-Account Access allows users or roles in one AWS account to securely access resources in another AWS account—without needing separate credentials. This capability is especially valuable in environments that follow modern cloud best practices around multi-account strategies.
Let’s break down some of the most common and practical use cases where this setup is a must-have.
1. Enterprises with Multi-Account Structure
Scenario: Large organizations often split workloads by environment—development, staging, and production—each residing in its own AWS account for security, billing, and access separation.
Why Cross-Account Access?
Instead of duplicating user accounts across environments, a centralized IAM role in the main account can assume roles into each of the other accounts. This ensures developers, testers, and ops teams only get access when they need it and to the resources they’re authorized to manage.
Example: A DevOps engineer in the main DevOps account assumes a role into the production account to push a deployment—without direct user credentials in prod.
2. Centralized Security, Auditing, and Logging
Scenario: Organizations often maintain a dedicated security account where CloudTrail logs, GuardDuty findings, Config snapshots, and audit reports are aggregated.
Why Cross-Account Access?
Each application account (Dev, QA, Prod, etc.) must grant read/write permissions to the security account to enable continuous compliance and visibility. Centralizing this data minimizes blind spots and ensures you meet auditing and compliance requirements like SOC 2 or ISO 27001.
Example: A Lambda function in the security account pulls logs from multiple accounts using cross-account roles with restricted access.
3. Managed Service Providers (MSPs) or Consultants
Scenario: MSPs and freelance DevOps engineers manage infrastructure across multiple client AWS accounts.
Why Cross-Account Access?
Instead of giving full user access or managing multiple IAM credentials, clients create a specific IAM role that the MSP can assume securely. This principle of least privilege reduces risk while allowing external partners to perform deployments, monitoring, or automation as required.
Example: An MSP accesses multiple client VPCs to perform security audits using a dedicated
SecurityAuditIAM role.
4. CI/CD Pipelines Across Accounts
Scenario: A centralized CI/CD system (e.g., GitHub Actions, Jenkins, GitLab CI) deployed in one AWS account needs to deploy applications into another AWS account.
Why Cross-Account Access?
The CI/CD tool assumes an IAM role in the target account with deployment permissions (e.g., access to ECS, EKS, Lambda, or S3). This decouples pipeline logic from sensitive production environments and enforces strict security boundaries.
Example: A GitHub Action running from the DevOps account assumes a deployment role in the Production account to update an ECS service with a new Docker image.
How Cross-Account Access Works (Step-by-Step)
- Create an IAM Role in Account B (resource owner).
- Attach necessary permissions policies to the role.
- Define a trust relationship to allow Account A (trusted account) to assume the role.
- In Account A, the user assumes the role via the AWS STS (Security Token Service).
Example:
// Trust policy in Account B
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::ACCOUNT-A-ID:root"
},
"Action": "sts:AssumeRole"
}
]
}Why Cross-Account Access is Better than Sharing IAM Users
When it comes to securely managing access in AWS, using IAM cross-account roles is a modern best practice that outclasses the outdated method of sharing IAM users. Let’s explore why.
1. Centralized Access Control
With IAM cross-account roles, all user identity and access management is centralized in one AWS account (often called the “identity account” or “master account”).
- Why it’s better: You control who can access what from a single pane of glass—without duplicating users across accounts.
- Real benefit: When a user leaves your organization, you just disable their main IAM account, and their access across all linked AWS accounts is instantly revoked.
In contrast, shared IAM users spread credentials across accounts, making revocation and permission updates painful and inconsistent.
2. Reduced Credential Sprawl
When using shared IAM users, teams often end up storing access keys in multiple places—local machines, Jenkins configs, or even hardcoded in scripts (which is very dangerous).
Cross-account roles eliminate this by using temporary credentials via the AWS Security Token Service (STS).
- Why it’s better: No need to manage static access keys, which are easy to lose, share, or accidentally leak.
- Real benefit: Reduces security risk and avoids “credential creep” where secrets get stored everywhere and nowhere securely.
Fewer secrets = less risk = safer cloud.
3. Enhanced Auditability via CloudTrail
Cross-account access leaves behind detailed CloudTrail logs in both the source and target accounts. Every time a role is assumed, it’s fully recorded with:
- The principal who assumed the role
- The originating IP and device
- The actions performed while using the role
- Why it’s better: You can track access history with clarity and correlate actions to specific users, even if the access came via automation or federation.
Shared IAM users? All actions show up under the same username—no idea which engineer actually made that S3 bucket public.
4. Scalability as Teams Grow
Cross-account roles are designed for scale. You can create reusable roles in each account and define which teams or services can assume them—without recreating identities or managing separate user pools.
- Why it’s better: Just onboard a new engineer in the central identity account and give them permission to assume roles into the accounts they need.
- Real benefit: Onboarding is fast, access is clean, and there’s no messy duplication.
With shared IAM users, you either over-provision a few user accounts or end up creating dozens of one-off users—both messy and insecure.
5. Separation of Duties
One of the pillars of cloud security is separating who can deploy, who can monitor, and who can audit.
Cross-account roles make this possible by assigning fine-grained permissions to different roles in different accounts—and then allowing only certain users or services to assume those roles.
- Why it’s better: A security analyst in the audit account can assume read-only roles, while a DevOps engineer assumes write roles in the deployment account.
- Real benefit: Limits risk and enforces least privilege access, which is a compliance and governance requirement for many companies.
Shared users tend to blur roles—often leading to over-permissioned accounts with too much power and too little oversight.
AWS IAM Cross Account Access Best Practices (2025 Edition)
1. Follow the Principle of Least Privilege
Only grant the minimum permissions necessary. Avoid wildcard * actions in policies. Use IAM Access Analyzer to validate permissions.
Example:
{
"Effect": "Allow",
"Action": ["s3:GetObject"],
"Resource": ["arn:aws:s3:::my-bucket-name/*"]
}2. Use IAM Roles Instead of IAM Users
IAM users are long-lived and harder to manage. IAM roles use temporary credentials, which reduce risk.
Bonus Tip: Always prefer short-lived credentials via
sts:AssumeRolewith proper session expiration.
3. Restrict Role Assumption Using Conditions
Enhance trust policies with Condition blocks to restrict access further. Use aws:SourceAccount, aws:PrincipalArn, aws:SourceIp, etc.
"Condition": {
"StringEquals": {
"aws:SourceAccount": "123456789012"
}
}4. Enable Multi-Factor Authentication (MFA) for Role Assumption
Add another layer of security by enforcing MFA when users assume roles.
"Condition": {
"Bool": {
"aws:MultiFactorAuthPresent": "true"
}
}5. Monitor Role Usage with AWS CloudTrail & CloudWatch
Audit who assumed which role, from where, and when. Set up alarms for suspicious activities.
Enable CloudTrail Insights for anomaly detection.
6. Tag Your IAM Roles
Use resource tags to manage and filter IAM roles easily, especially in large environments.
"TagKey": "Environment",
"TagValue": "Production"7. Use Permission Boundaries for Managed Delegation
If you delegate permissions to teams, define permission boundaries to control the maximum permissions a role can get, even if overly permissive policies are attached.
8. Secure Cross-Account S3, Lambda, and KMS Access
Services like S3 and KMS often support resource-based policies. Combine these with IAM roles for precise control.
Example — S3 bucket policy for cross-account access:
{
"Sid": "CrossAccountAccess",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::ACCOUNT-A-ID:role/MyCrossAccountRole"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::my-secure-bucket/*"
}9. Rotate Access Keys (Only If Necessary)
If you must use access keys (e.g., CI/CD tool limitations), rotate them regularly and audit via IAM reports.
10. Document and Automate Everything
- Maintain a Confluence or GitHub doc for each cross-account role.
- Use IaC tools like Terraform or AWS CloudFormation to manage IAM configurations.
Please read this our most valueable article, How to setup AWS GuardDuty in for Production
Troubleshooting Common Cross-Account Access Issues
| Issue | Cause | Fix |
|---|---|---|
AccessDenied error | Incorrect trust policy or permission | Validate both trust and access policies |
| STS AssumeRole fails | Missing IAM permissions | Ensure user/role has sts:AssumeRole |
| Unintended access | Wildcard permissions (*) used | Use least-privilege approach |
Automating Cross-Account Access Setup with Terraform (Optional)
For DevOps engineers, using Terraform makes IAM role creation, policy assignment, and trust relationships easier and version-controlled.
Example:
resource "aws_iam_role" "cross_account_role" {
name = "CrossAccountReadOnly"
assume_role_policy = jsonencode({
Version = "2012-10-17",
Statement = [{
Effect = "Allow",
Principal = {
AWS = "arn:aws:iam::ACCOUNT-A-ID:root"
},
Action = "sts:AssumeRole"
}]
})
}Final Thoughts: Build Cross-Account IAM Access Securely in 2025
AWS IAM cross-account access is an essential practice for secure multi-account cloud architectures. By following best practices like least privilege, MFA enforcement, and continuous monitoring, you can build a secure, compliant, and scalable AWS environment.
Pro Tip: Document and review cross-account roles regularly. AWS security is never a “set and forget” practice.
FAQs on Cross-Account IAM Access
Q. Can I assume a role in another AWS account from the AWS CLI?
Yes. Use the sts assume-role command and pass the role ARN.
Q. How long are STS credentials valid?
By default, up to 1 hour (3600 seconds). Configurable up to 12 hours with session policies.
Q. Should I use resource policies or IAM policies?
Use both when possible. IAM policies control who can assume, and resource policies control what they can do.
Q. How do I enforce MFA for cross-account access?
Attach an IAM policy that includes a condition requiring aws:MultiFactorAuthPresent it to be true during role assumption.
Q. Can I restrict cross-account access to specific services or actions?
Yes, always apply least privilege by specifying only the required actions (Action) and resources (Resource) in the trust and permission policies.
Q. How do I audit or monitor cross-account access?
Use AWS CloudTrail, CloudWatch Logs, and Access Analyzer to track and review cross-account activity.
Conclusion
Managing permissions across multiple AWS accounts isn’t just a technical necessity—it’s a strategic move for growing cloud teams. As someone who’s worked with DevOps and cloud security for years, I’ve seen firsthand how implementing cross-account IAM access simplifies audits, improves security posture, and fosters team independence. It’s not always easy to get right, but when done well, it sets the foundation for a truly scalable and secure AWS environment. Start small, follow these best practices, and scale smartly—your future self (and your security team) will thank you!