In today’s cloud-driven world, securing your AWS infrastructure is not optional — it’s critical. As threats continue to evolve, relying solely on traditional firewalls or basic monitoring isn’t enough. That’s where AWS GuardDuty comes in — a powerful threat detection service that continuously monitors your AWS environment and helps you respond quickly to suspicious activities.
In this blog post, we’ll walk you through everything you need to know about how to set up AWS GuardDuty for production environment. Whether you’re a DevOps engineer, security specialist, or cloud architect, this guide will equip you with practical steps and best practices to harden your AWS accounts using GuardDuty.
What is AWS GuardDuty?
AWS GuardDuty is a managed threat detection service that uses machine learning, anomaly detection, and integrated threat intelligence to identify malicious or unauthorized behavior in your AWS accounts, workloads, and data.
It continuously analyzes AWS CloudTrail logs, VPC Flow Logs, and DNS logs to flag unusual activity like:
- Unusual API calls
- Unauthorized access attempts
- Compromised EC2 instances
- Crypto mining activities
In simple words: GuardDuty acts like a smart security camera for your AWS environment.
Why Use GuardDuty in Production?
Securing a production environment in AWS is not just about blocking access — it’s about early detection of threats. GuardDuty excels in:
- 24/7 continuous monitoring
- Minimal false positives using ML-based behavior analysis
- Integration with AWS Security Hub, CloudWatch, EventBridge, and Lambda for automated remediation
- No agents required on your EC2 or containers
- Multi-account protection using AWS Organizations
So, if you’re building or managing a production workload in AWS, enabling GuardDuty gives you peace of mind and a stronger compliance posture.
Prerequisites Before Setup
Before you enable GuardDuty in a production environment, make sure:
- You have an AWS Organization (for multiple accounts)
- You are logged in as an IAM user or root with sufficient privileges
- You know the AWS Region(s) where production resources reside
- You have enabled CloudTrail and VPC Flow Logs (optional but recommended)
Step-by-Step Guide: How to Set Up AWS GuardDuty for Production
Step 1: Enable GuardDuty in the AWS Console
- Sign in to the AWS Console.
- Go to Amazon GuardDuty (you can search for it in the Services menu).
- Click on “Enable GuardDuty”.
- GuardDuty will automatically start analyzing data sources like CloudTrail, DNS logs, and VPC Flow Logs.
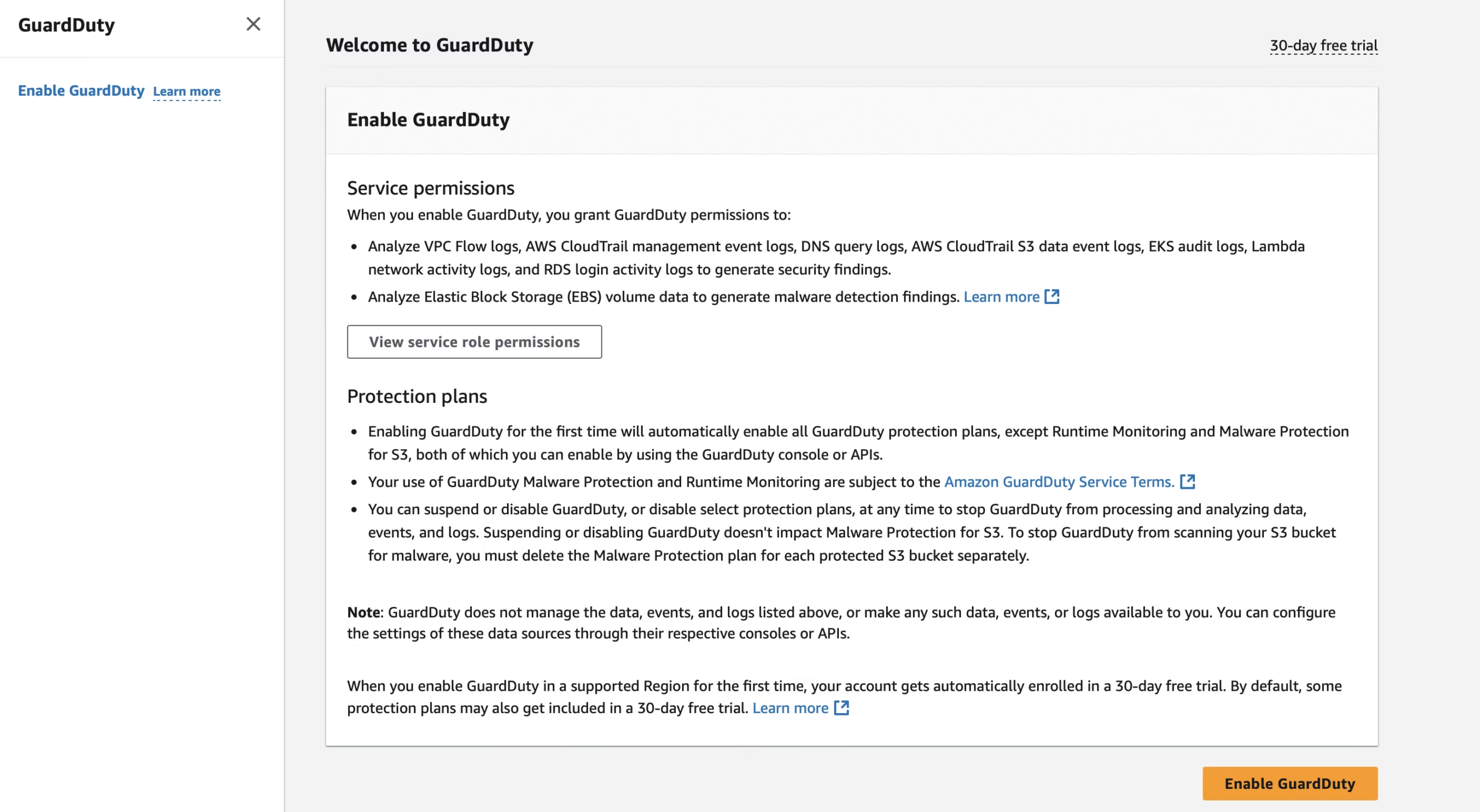
No need to configure anything right away — GuardDuty is agentless and starts operating immediately.
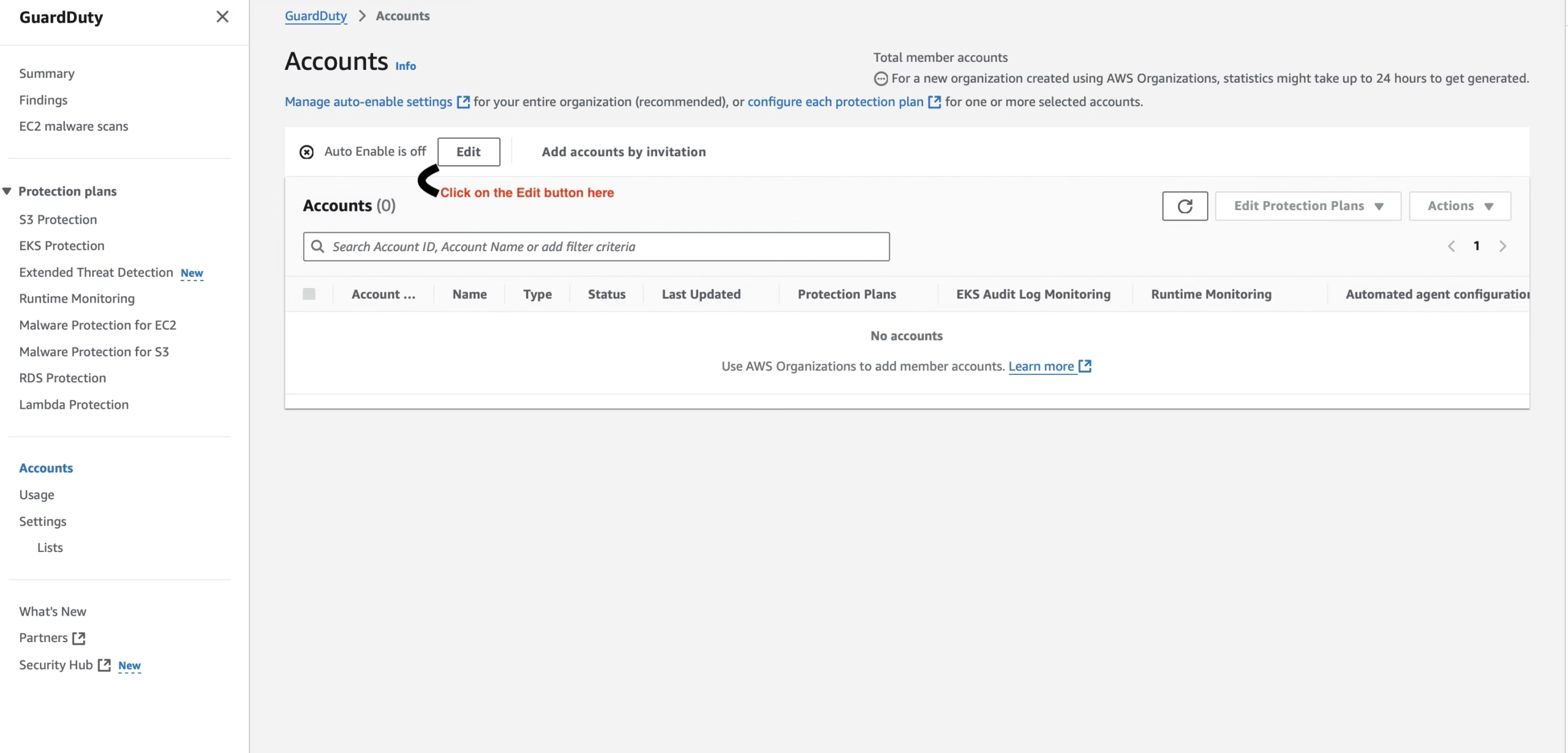
Step 2: Set Up Organization-Wide Detection (Multi-Account Setup)
In production, it’s common to use multiple AWS accounts under AWS Organizations. GuardDuty supports delegated administration so you can monitor all linked accounts from a single management account.
How to Set It Up:
- Go to the GuardDuty console in the Management Account.
- Click on “Accounts” → “Manage accounts with AWS Organizations”.
- Choose to auto-enable GuardDuty for new AWS accounts.
- Select which accounts to monitor.
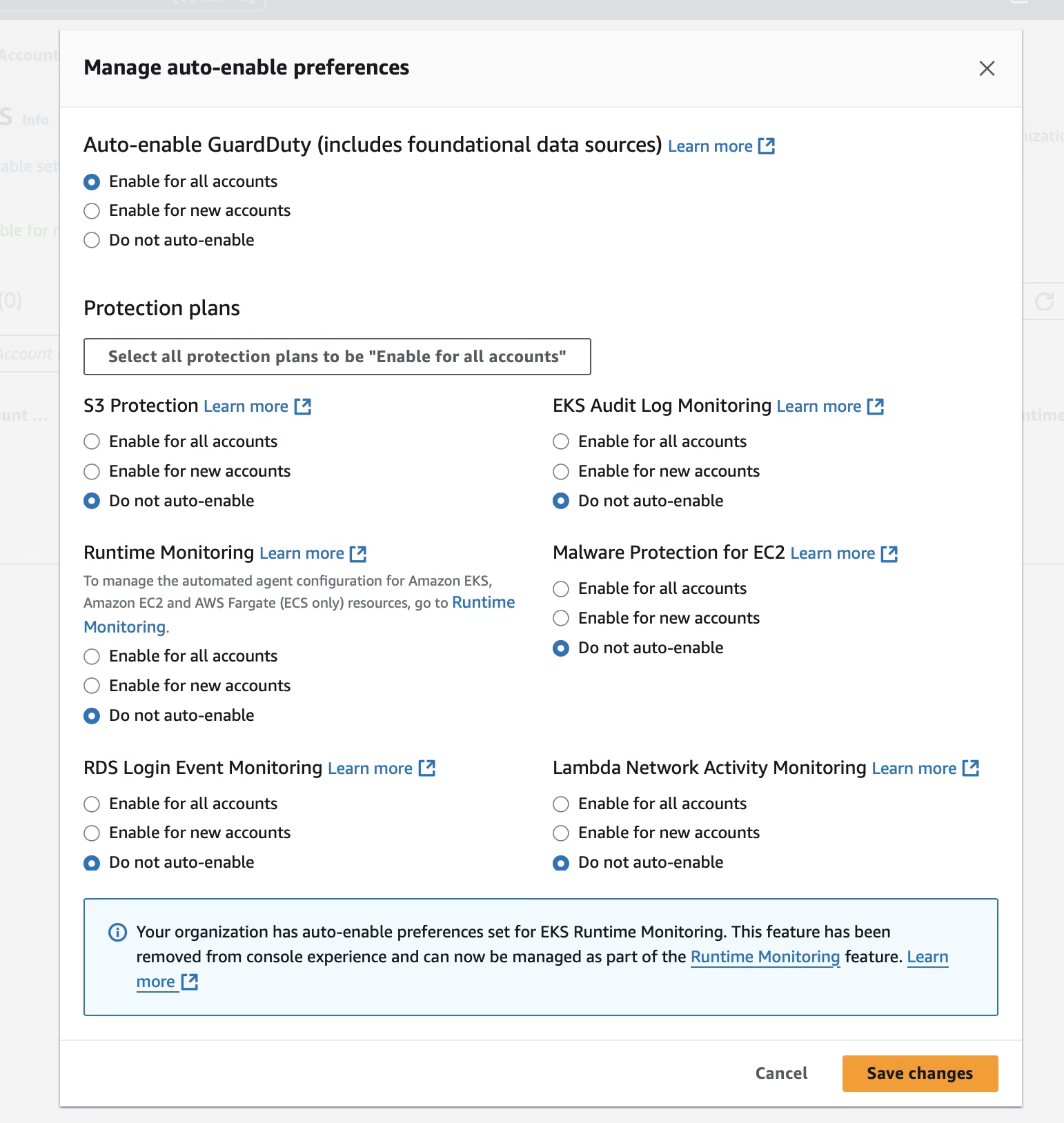
Once you click on the Edit button, it will display the next window, the auto-enabled setting preference window. You need to select your preference for enabling all accounts or new accounts, and also select the protection plans.
This helps ensure centralized visibility across all production environments.
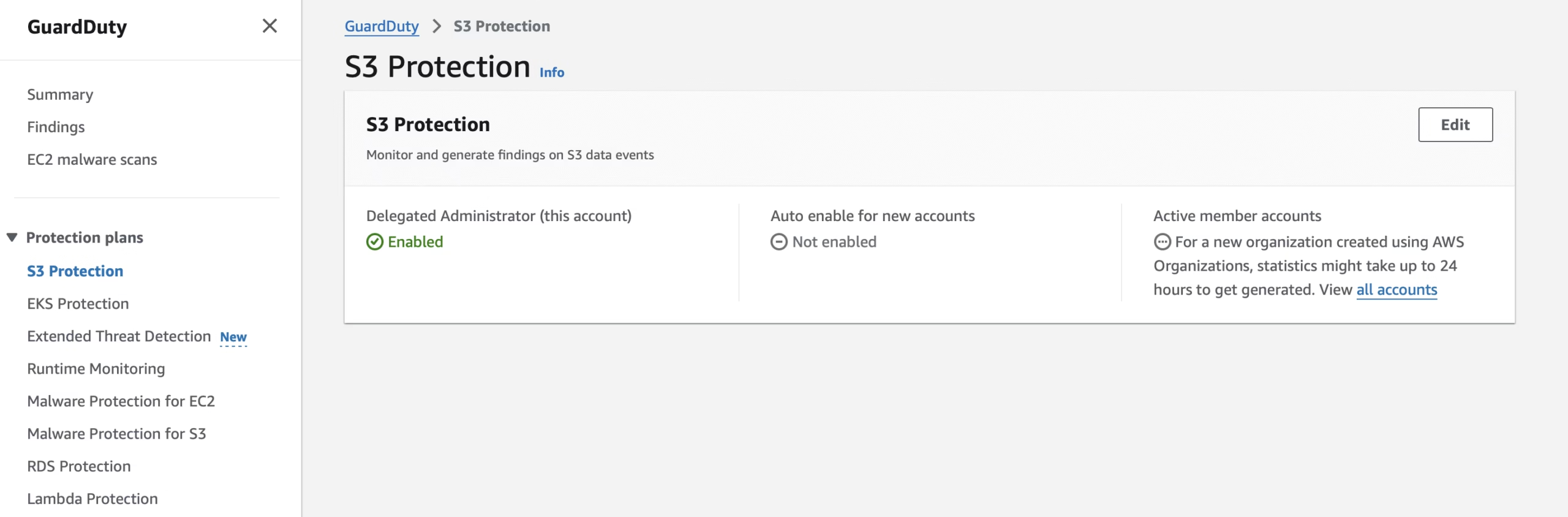
Step 3: Configure S3 Protection
S3 protection is not enabled by default. You need to turn it on:
- Go to GuardDuty → Settings
- Enable S3 Protection
- This enables monitoring of suspicious API calls and anomaly behavior in your S3 buckets
Step 4: Enable Kubernetes Protection (Optional but Recommended)
If you’re using EKS in production, enable Kubernetes threat detection:
- In GuardDuty → Settings → Kubernetes Protection
- Turn on Audit Log Monitoring
- Integrate with your EKS clusters
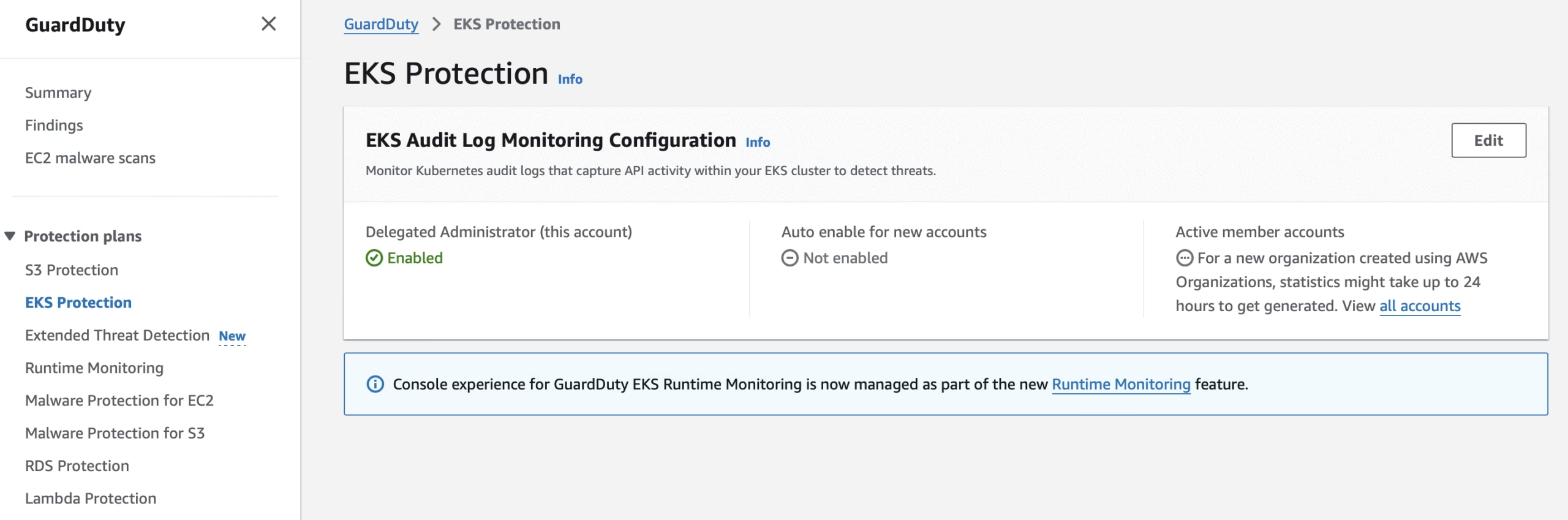
This helps detect container breakout attempts, privilege escalation, or abuse of kubelet APIs.
Step 5: Enable All Available Data Sources
GuardDuty works best when it has access to all the relevant logs.
Make sure you enable these data sources on the auto-enable preference window or from the protection plans on the left side of the GuardDuty window.
| Data Source | Description |
|---|---|
| CloudTrail | Detects unusual API calls or unauthorized usage |
| VPC Flow Logs | Detects suspicious network traffic |
| Route 53 Logs | Detects DNS exfiltration, fast-flux domains, etc. |
| EKS Audit Logs | Detects suspicious container activities (if using EKS) |
| S3 Logs | Detects unauthorized data access or public exposure |
Step 6: Integrate GuardDuty with AWS Security Hub
To create a central security dashboard, integrate GuardDuty with AWS Security Hub.
- Go to the Security Hub console
- Enable it if it’s not already active
- Go to Integrations → Amazon GuardDuty → Enable
This ensures all findings are aggregated and can be correlated with other AWS security tools like Macie or Inspector.
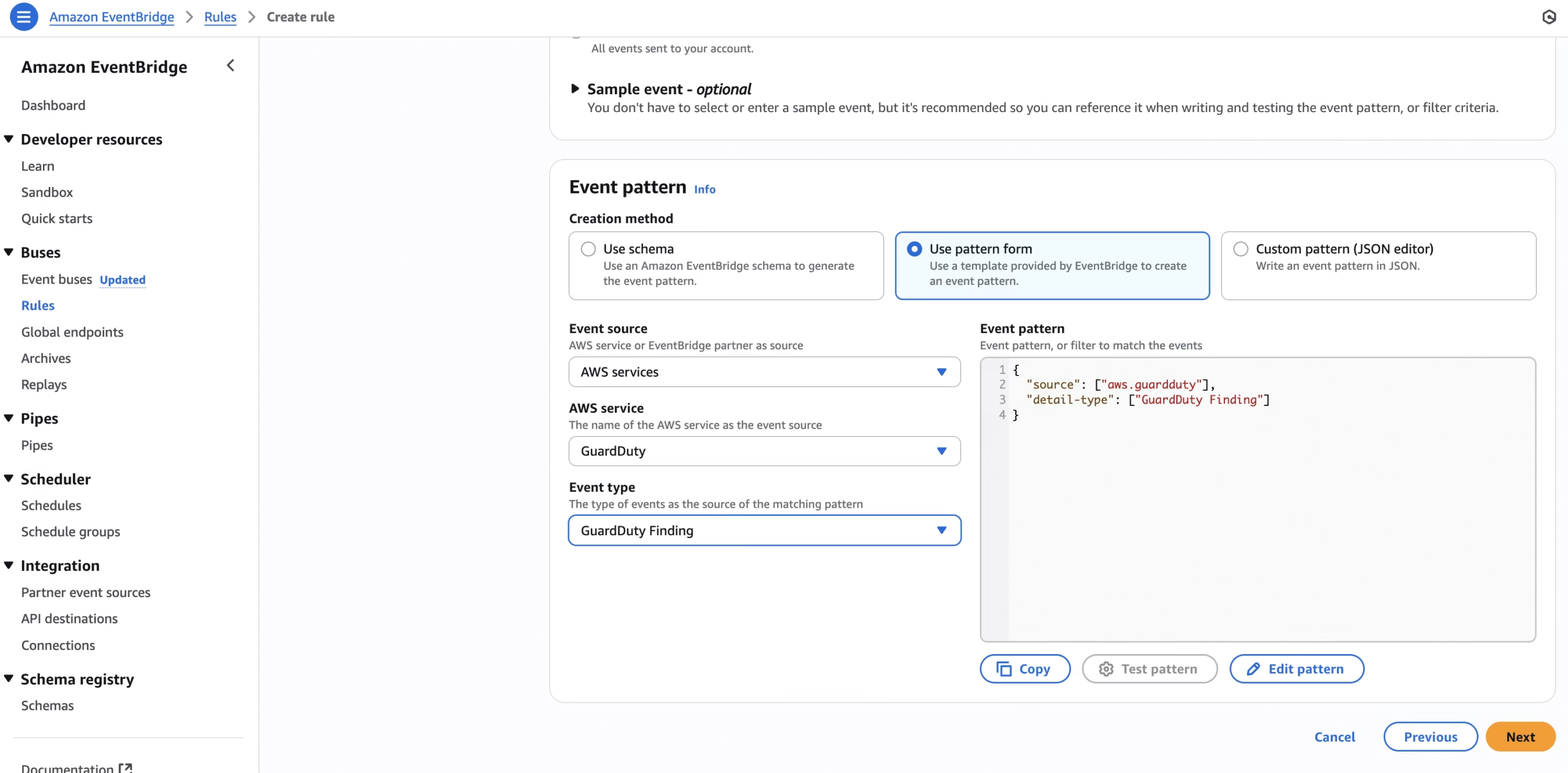
Step 7: Set Up Automated Alerts and Remediation
To avoid missing critical alerts, you should integrate GuardDuty with:
- Go to EventBridge → Rules
- Create a new rule with GuardDuty Finding as the event pattern
- Add SNS, Lambda, or EventBridge as a target to take action (e.g., isolate a compromised EC2)
Example Use Case:
When GuardDuty detects that an EC2 instance is communicating with a known malicious IP, you can automatically shut down the instance or revoke its
You can create a rule in EventBridge:
{
"source": ["aws.guardduty"],
"detail-type": ["GuardDuty Finding"],
"detail": {
"severity": [8, 9]
}
}Trigger a Lambda function to take automated action, such as quarantining resources or notifying your SecOps team.
Sample Use Cases from Production Environments
- Detecting credential compromise: An IAM user from your dev team suddenly starts accessing production S3 buckets from an IP in a different country? GuardDuty will alert you.
- Reconnaissance activity: GuardDuty can catch port scans before an attacker finds vulnerabilities in your EC2 instances.
- Botnet communication: It can detect if an EC2 instance is part of a botnet, reaching out to known command-and-control IPs.
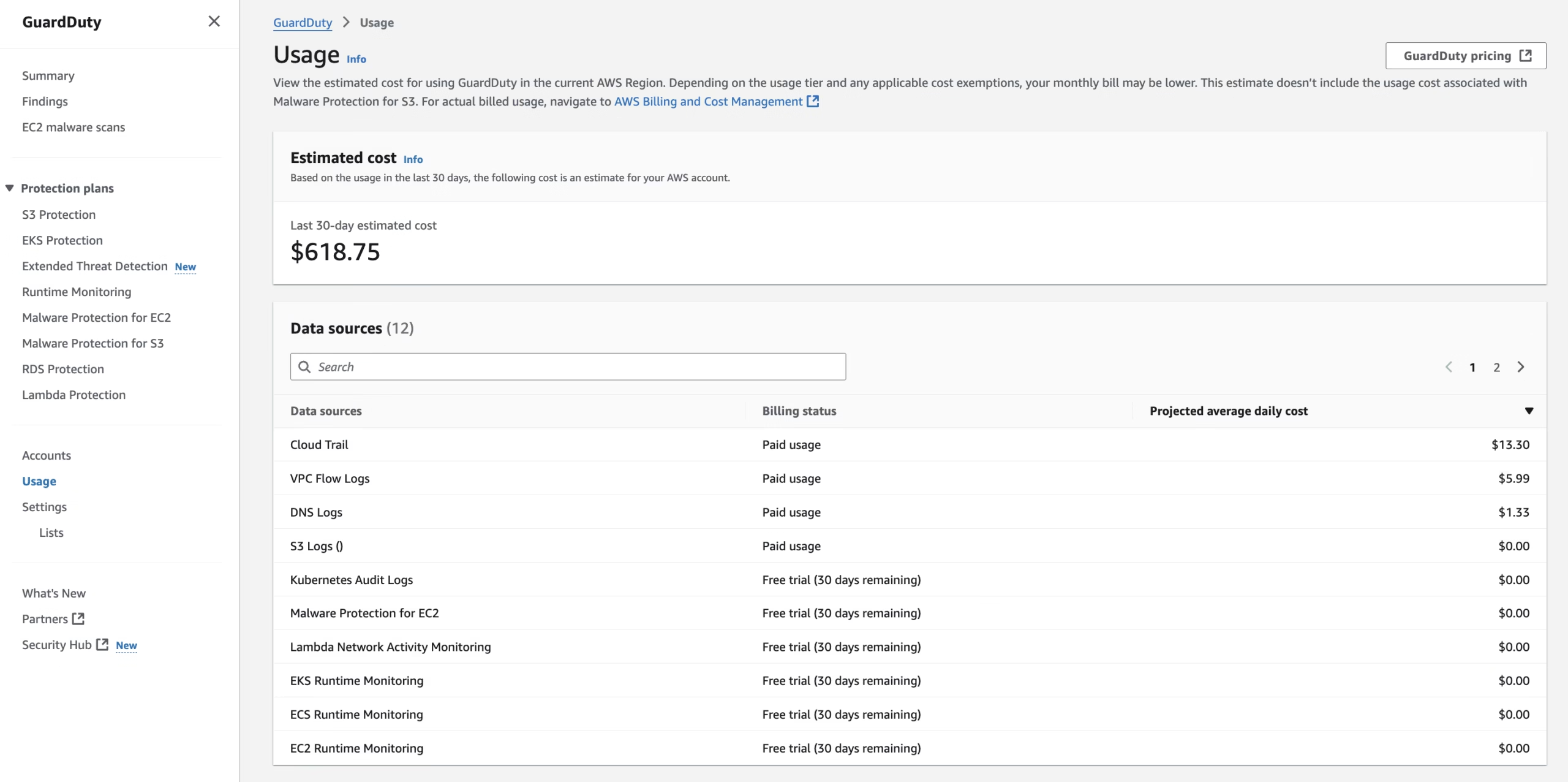
How Much Does GuardDuty Cost?
GuardDuty charges are based on:
- The volume of VPC Flow Logs, DNS logs, and CloudTrail events it analyzes
- Number of regions enabled
Tip: You can estimate costs using the AWS Pricing Calculator.
You can check the GuardDuty usage cost in the GuardDuty Usage/Cost info.
Best Practices for Production
- Enable GuardDuty in ALL AWS regions — Even if you don’t use them. Attackers may exploit unused regions.
- Auto-enable for new accounts — Especially in production environments using AWS Organizations.
- Use tags to classify findings — Helps in sorting and prioritizing threats.
- Periodically review findings — Create a weekly or daily security review pipeline.
- Combine with IAM Access Analyzer — To catch overly permissive roles.
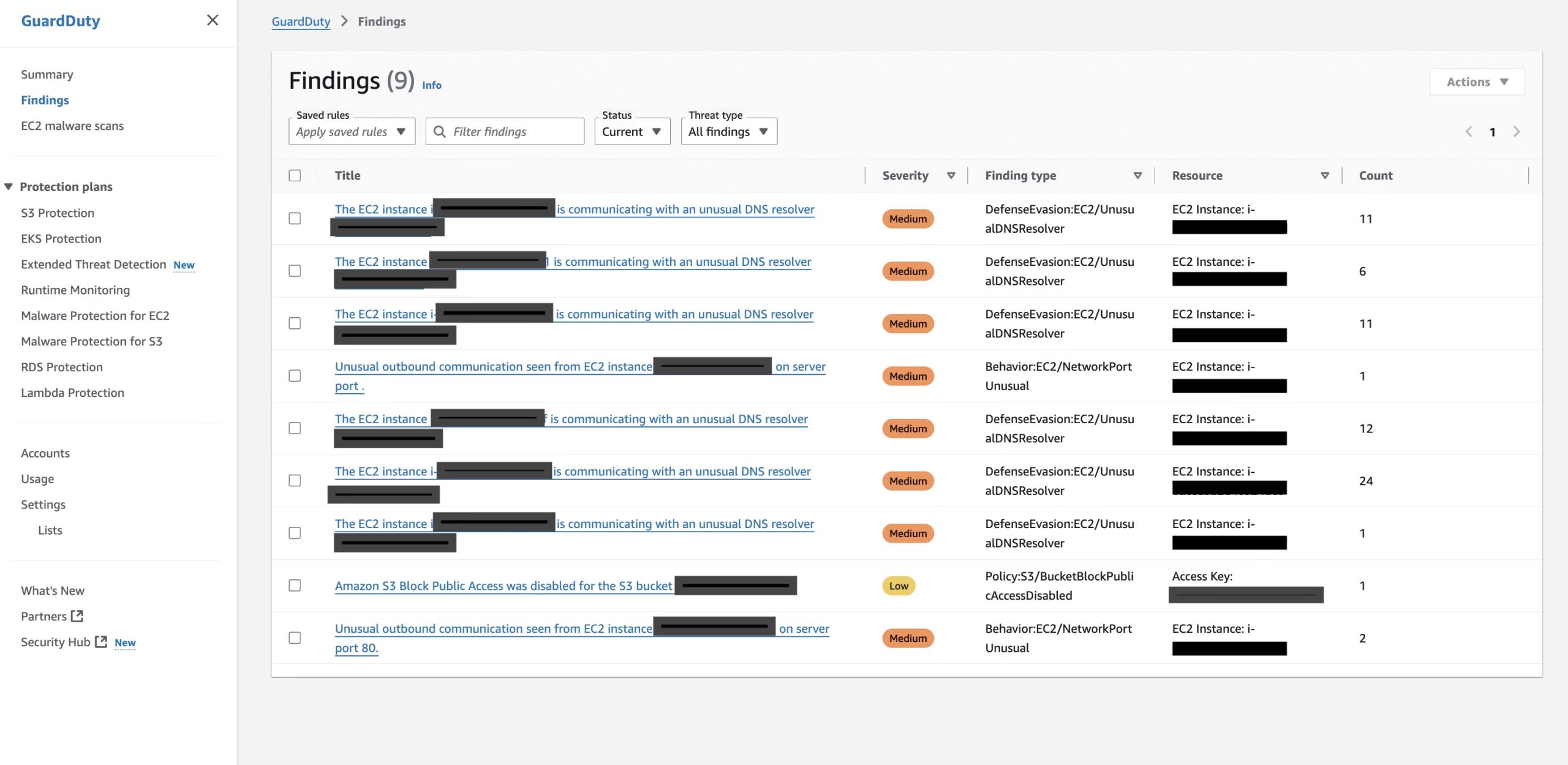
Common GuardDuty Findings in Production
| Finding Type | Example | Severity |
|---|---|---|
| Recon:EC2/PortScan | External IP scanning ports | Medium |
| UnauthorizedAccess:IAMUser | Usage of stolen credentials | High |
| CryptoCurrency:EC2/BitcoinTool | Mining detected on EC2 instance | High |
| Trojan:EC2/BlackholeTraffic | Malware-infected outbound traffic | High |
| Policy:S3/BucketPublicAccess | Public S3 bucket flagged | Medium |
Some of the real Production environment findings are mentioned below.
Please read our most valueable article about How do we host static website in AWS S3
Conclusion
AWS GuardDuty is not just another AWS service—it’s a must-have for any production-grade AWS setup. It provides continuous security monitoring without the hassle of deploying and managing infrastructure.
Whether you’re running EC2 instances, Lambda functions, or storing critical data in S3, GuardDuty helps ensure you’re aware of threats as soon as they happen. Set it up today and secure your cloud before attackers find a way in.
FAQs
Q1: Does GuardDuty add cost?
Yes, but it’s usage-based. The cost is relatively low compared to the risk of undetected threats.
Q2: Does GuardDuty impact performance?
No. It’s completely agentless and doesn’t run on your infrastructure.
Q3: Do I need to write custom detection rules?
No. GuardDuty has built-in intelligence and machine learning models that evolve automatically.
Q4: Can I use GuardDuty without AWS Organizations?
Yes, but it’s harder to manage at scale. AWS Organizations is the best approach for production.
Q5: How do I test if GuardDuty is working?
AWS provides sample findings in the GuardDuty console for testing alerting pipelines.
Discover more from DevOpsHowTo.Com
Subscribe to get the latest posts sent to your email.

1 thought on “How to Set Up AWS GuardDuty for Production (Step-by-Step Guide)”